Achieving your SWIFT CSP Compliance attestation in 2025 is still a marathon, not a sprint. But with a clear roadmap, the journey feels far less painful. Use the five‑part playbook below to glide from “Where do we start?” to a clean, on‑time submission, without the eleventh‑hour panic.

Scope the Environment

Map every asset and data flow
List every interface that can send, store, or even brush against SWIFT messages—Alliance Access, Lite2, messaging hubs, jump hosts, HSMs, cloud analytics, you name it. Tag each item In‑Scope or Out‑of‑Scope in your CMDB and keep the list tied to your SWIFT CSP controls checklist.
Draw diagrams that speak for themselves
A single picture of network zones, trust boundaries, and message paths helps an assessor decide in seconds which nodes inherit SWIFT CSP requirements. Update the diagram quarterly; mergers and new APIs appear faster than you think.
Apply the MECE rule
Make sure your scope is Mutually Exclusive, Collectively Exhaustive. That means production, DR, test, on‑prem, cloud, and outsourced service bureaus all get the spotlight. Document why anything is excluded (for example, “UAT holds no live SWIFT keys”) to avoid debate later.
Learn the 2025 control set
CSCF v2025 contains 32 controls—25 Mandatory (M) and 7 Advisory (A). The newest Mandatory is 2.8 M — Outsourced Critical Activity Protection. Keep an eye on 2.4 A (Back‑Office Data Flow Protection); SWIFT has flagged it to become Mandatory in 2026. Treat Advisory items as tomorrow’s Mandatories and plot effort versus impact on a simple heat map.
Run a gap assessment you can trust
Copy every control into a spreadsheet, add real‑world evidence examples, and assign an owner. Score gaps on a 3 × 3 matrix: High‑Impact/Low‑Effort fixes become Quick Wins; High‑Impact/High‑Effort items become Strategic projects. Review progress every two weeks—no more year‑end fire drills.
Harden High‑Risk Assets

Identify Tier‑0 systems
Alliance servers, payment‑approval workstations, SWIFTNet Link, and signing HSMs are your crown jewels. Grade each one on criticality, connectivity, external exposure, and patch age. Anything scoring 15 or higher gets hardened first.
Patch early, patch often
Control 2.2 demands critical patches within 30 days; many banks aim for under 10. Automate where you can and track patch age in days, not weeks.
Lock down applications
Mandatory Control 2.1 insists that only approved binaries run on messaging endpoints. Roll out AppLocker or Carbon Black in audit mode for two weeks, then flip the enforcement switch.
Add modern EDR
While Endpoint Detection & Response is still Advisory (Control 2.11), it has become a de facto expectation for meeting Principles 6 and 7. Deploy an EDR agent that can isolate a host the moment it spots tampering—this slashes investigation time and strengthens evidence for Controls 6.1 and 6.4.
Segment like you mean it
Place Tier‑0 assets on dedicated VLANs, enforce default‑deny firewalls, and consider data diodes for one‑way transfers. Every packet must prove it belongs.
Layer controls, never rely on one
Firewall + Segmentation + MFA + EDR + HSM equals a security stack that meets multiple SWIFT CSP requirements at once—and gives auditors a clear, defensible story.
Secure the Supply Chain

List every external touchpoint
Service bureaus, correspondent banks, managed SOCs, SAP connectors—the whole lot. Record connection type, data exchanged, auth method, and contract owner so nothing slips through the cracks.
Trust, but verify
Ask vendors for their own SWIFT CSP attestation or a SOC 2 report. Self‑signed PDFs don’t count. Calendar renewal dates so that expired evidence never surprises you during assessment.
Write security into contracts
Insert clauses for right‑to‑audit, 24‑hour breach notice, and patch cadences that mirror your own. Failure to stay compliant becomes a material breach—it’s that simple.
Stand-up technical guardrails
Vendor tunnels land in a DMZ, VPNs require MFA, and least‑privilege accounts use a monitored jump host. Pipe all third‑party traffic into your SIEM to feed the wider SWIFT security program implementation.
Align with Control 2.8 M
Since 2025, outsourcing critical activities triggers the new Mandatory Control 2.8. Prove that outsourced providers are subject to the same safeguards, monitoring, and rapid patching you apply internally.
For tailored guidance and implementation support, visit our dedicated SWIFT CSP compliance services page.
Continuous SWIFT CSP compliance monitoring
Policy library, procedure playbook
Every control needs a governing document. Use one template—objective, scope, roles, review cadence—so assessors can map controls to pages instantly. Translate policies into task‑level procedures (e.g., “Patch Tier‑0 servers in 24 hours; ticket ID in ServiceNow”) and store both in a central vault.
Automate evidence collection
Screenshots age fast. Instead, script exports or leverage APIs to drop logs, configs, and dashboards into a read‑only repository. Name files ControlID_EvidenceType_Date.pdf—Auditors love consistency.
Train the humans
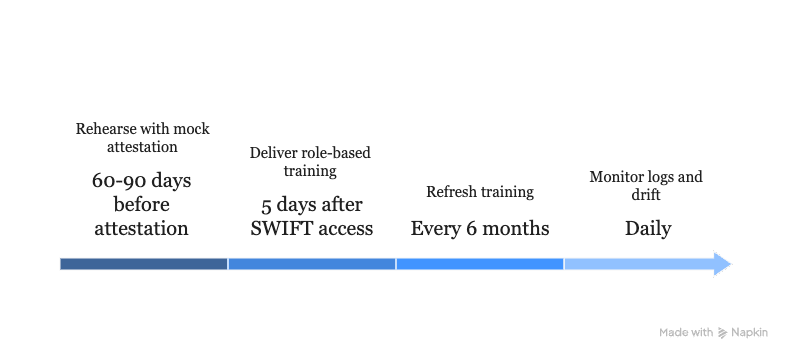
Security controls crumble when people skip steps. Deliver role‑based training within five days of SWIFT access and refresh every six months. Mix short CBTs, live phishing drills, and brown‑bag Q&As. Log attendance in your LMS; it’s Mandatory under Governance Control 8.2.
Monitor everything, all the time
Control 6.4 calls for continuous log monitoring. A SIEM rule pack tagged with CSCF IDs plus nightly drift scans (Ansible, InSpec, or SCCM DSC) shows you—and the assessor—exactly where you stand. Dashboards that track MTTD, MTTR, and patch latency turn raw data into board‑ready metrics.
Rehearse with a mock attestation
Run the full questionnaire 60–90 days before the real deal. Answer every control out loud, show the evidence, and time each response. Flag missing artefacts, open remediation tickets, and lock them down before the independent assessor arrives.
Attest, Improve, Repeat
Know the attestation window
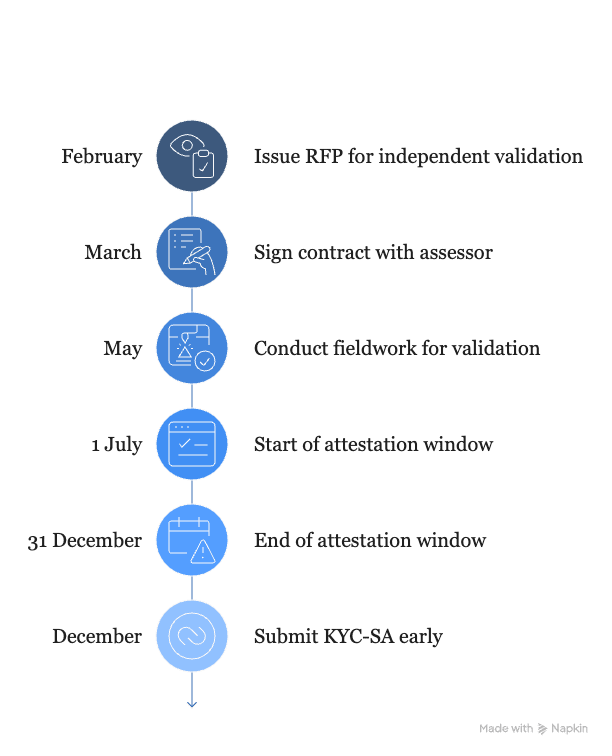
You must re‑attest each year between 1 July and 31 December. Miss 31 December and SWIFT marks you non‑compliant.
Book the assessor early
Independent validation is mandatory. Issue an RFP in February, sign in March, fieldwork in May; that leaves two full remediation cycles before the window opens on 1 July.
Deliver a polished evidence bundle
Package the updated network diagram, SWIFT control gap assessment spreadsheet, policies, and SOC metrics on day one of fieldwork. Teams that do this cut on‑site days by 30 per cent.
Secure senior management sign‑off
Board‑level approval is mandatory. Present a one‑page heat map of any “Partially Compliant” controls, gain written acceptance of residual risk, and archive the email with your evidence.
File in KYC‑SA early
December is a traffic jam. Submit at least three weeks before year‑end, download the confirmation PDF, and store it in your vault. Late filings can lead to restricted messaging or, worse, suspension.
Lock in continuous improvement
Quarterly mini‑audits, monthly metric reviews, and automatic alerts for control drift turn SWIFT CSP compliance from an annual scramble into muscle memory. Feed every lesson back into the risk register, update policies, and retest. That loop is your cheapest insurance policy against the next wave of fraud tactics.
In short
Achieving SWIFT CSP compliance is tough, but it doesn’t have to be chaotic. Map the footprint, close the gaps, harden what matters, prove it with evidence, and keep the wheel turning. Follow these 14 steps—grouped into five easy‑to‑manage phases—and you’ll glide through the CSP process, earn your attestation on time, and build a security posture that can stand up to tomorrow’s threats.
For the official definitions, see SWIFT’s own SWIFT CSP framework v2025 — the authoritative source on SWIFT CSP compliance requirements.
