The EU’s Digital Operational Resilience Act (DORA) signifies a landmark regulatory drive to bolster ICT resilience throughout Europe’s financial sector. DORA introduces rigorous standards around risk management, incident reporting, and resilience testing, fundamentally shifting how financial institutions and ICT service providers must approach digital risk. But how can you effectively prepare?
Fortunately, in this article, we unpack 7 actionable, practical DORA compliance tips that your financial organisation can implement today—ensuring a smooth transition to greater operational resilience.
DORA Compliance Tip 1: Understand the Scope and Applicability
To kickstart your organisation’s compliance, understanding exactly where you stand within DORA’s landscape is simply non-negotiable.
Officially enacted as Regulation (EU) 2022/2554, DORA applies across numerous financial entities (Eur-lex), including:
- Credit institutions: banks and lending organisations.
- Investment firms: brokerage houses, trading platforms, and asset managers.
- Payment service providers: digital processors and electronic money issuers.
- Insurance and reinsurance companies: firms underwriting risks.
- Pension funds: managing retirement investments.
- Third-party ICT providers: technology companies supplying essential ICT services.
Yet here’s the kicker—the EU specifically incorporates a principle of proportionality. Smaller or simpler organisations can scale compliance based on their unique capacities and risk profiles.
Practically speaking, carefully evaluate your internal business activities, third-party relationships, and overall risk profile. Document precisely where you fall in the regulatory scope. For instance, a fintech payment startup will likely adopt simplified measures, such as streamlined incident management processes, whereas multinational banking groups require layered, robust risk management frameworks.
Clearly documenting your categorisation and scalability decisions ensures no regulatory “grey areas,” setting your compliance journey off on solid footing.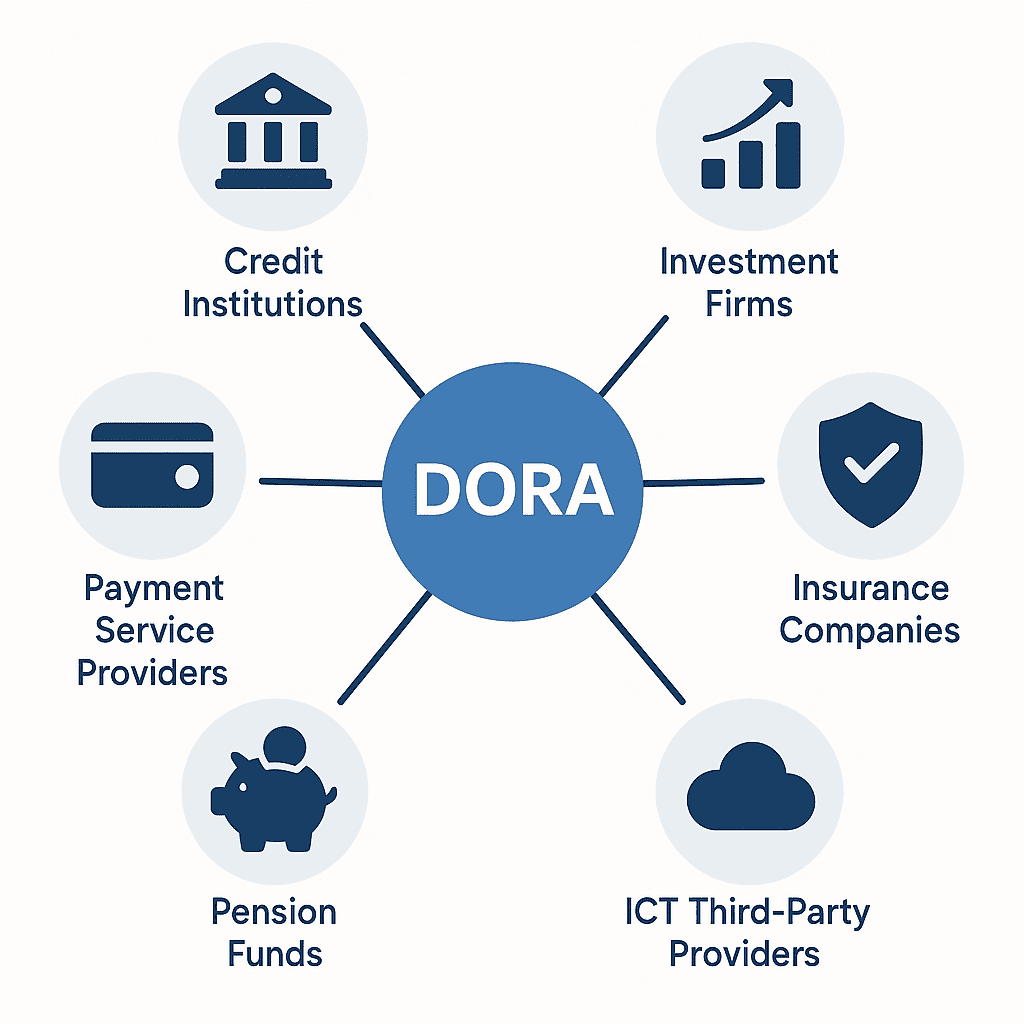
DORA Compliance Tip 2: Building an ICT Risk Management Framework
But understanding your scope alone won’t cut it. DORA requires financial institutions to establish a comprehensive ICT risk management framework—organised, clearly structured, and deeply integrated across your organisation.
Here’s exactly how to build your risk management framework:
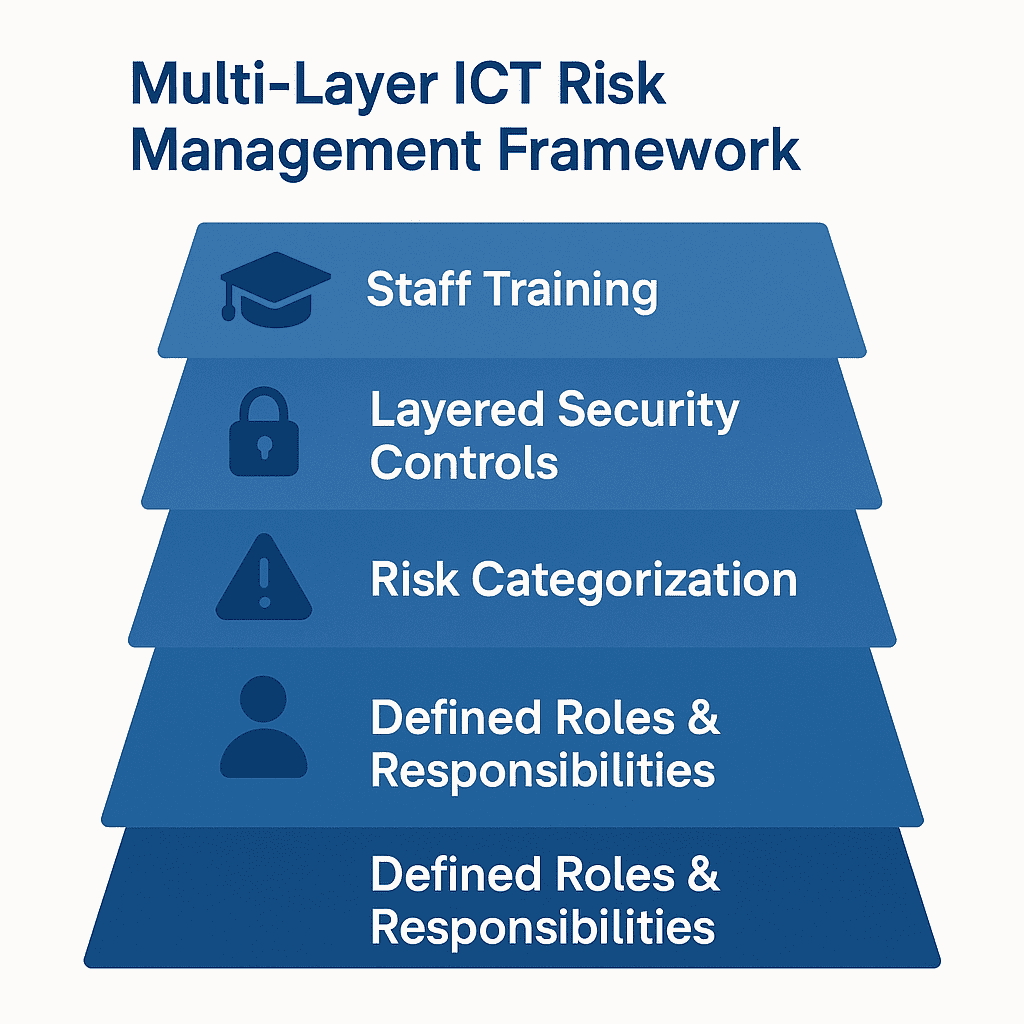
Define Clear Roles & Responsibilities
Detail precise ICT roles—from senior management to IT and security staff—so there’s no guesswork when incidents arise. Clear accountability accelerates decision-making and fosters greater preparedness.
Set Strict, Actionable Risk Thresholds
Carefully define tolerable risk limits, like maximum service downtime or acceptable data loss levels. Revisit regularly—because technology threats evolve quickly and unpredictably.
Continuously Identify & Categorise ICT Risks
Group ICT threats into clear categories, such as cybersecurity threats, operational outages, vendor risks, and human errors. Regular scans and external intelligence services help maintain updated vulnerability databases.
Layer Up Security Controls
Deploy multi-layered security measures—encryption, MFA, network segmentation, robust access controls—positioning your company to resist both internal and external threats.
Invest in Staff Training & Awareness
Implement regular internal training and simulated exercises. Staff who recognise phishing attempts and adhere to secure device and remote-use guidelines significantly reduce your risk exposure.
By systematically embedding these essential elements within your broader risk management practice, your institution moves beyond simple compliance towards genuinely fortified resilience.
DORA Compliance Tip 3: Implement Effective Incident Reporting Processes
Next up? Incident reporting. Under DORA, financial companies must swiftly detect, escalate, and externally report ICT incidents to regulators. Fumbling on incident handling is more than just a regulatory misstep—it’s a reputational disaster waiting to happen.
How do you avoid the pitfalls?
Establish Clear Internal Escalation Paths
Clearly map out escalation criteria, roles, and timelines. Define exactly when and how incidents progress from detection towards immediate regulatory reporting.
Automate Incident Detection & Reporting
Adopt automated SIEM or IDS solutions such as Splunk or PagerDuty, designed for swift event detection, classification, escalation, and documentation. Leveraging such tools maintains real-time incident responsiveness.
Run Regular Crisis Simulations
Practice realistic cyber breach scenarios quarterly (such as ransomware attacks or payment outages), ensuring familiarity across your institution with processes, roles, and reporting requirements.
Taken together, these actions ensure your incident reporting remains seamlessly compliant and operationally effective, reducing both regulatory and reputational risk during critical incidents.
DORA Compliance Tip 4: Conduct Resilience Testing and Continuous Monitoring
However, maintaining digital resilience demands more than a one-off compliance exercise; it requires continual testing and monitoring. EU DORA obligates institutions to regularly evaluate their ICT resilience through realistic scenario-driven assessments.
For optimal results:
- Incorporate continuous monitoring tech (SIEM, EDR, IDS) to identify threats instantly.
- Regularly test your core systems—simulate outages, cyber attacks, or third-party vendor failures reflecting realistic sector threats.
- Engage external, independent security testers occasionally (like Threat-Led Penetration Tests, TLPT) to avoid internal biases and uncover hidden vulnerabilities.
This proactive approach moves beyond bare-minimum compliance, actively strengthening your defences through adaptability and continuous improvements.
DORA Compliance Tip 5: Strengthen Third-Party ICT Risk Management
Let’s face it—today, financial institutions increasingly rely on third-party ICT services. While efficient, these partnerships also bring significant dependency risks. DORA emphasises explicit due diligence of third-party service providers.
To manage third-party risk effectively:
- Add explicit resilience mandates and incident-handling obligations into contracts.
- Regularly audit vendors’ cybersecurity posture for compliance, including penetration testing and vulnerability scanning.
- Establish contingency plans—identifying alternate providers or recovery strategies if critical vendors fail—thus safeguarding service continuity.
Clearly, proactively managing third-party risks is no longer just sensible—it’s mandatory under DORA.
DORA Compliance Tip 6: Align Governance and Management Structure
Beyond operational tactics, effective oversight is foundational. Explicitly assign senior executive accountability for digital operational resilience.
To achieve alignment:
- Clearly define board-level accountability (like assigning a CISO reporting directly to executives).
- Implement transparent, standardised internal reporting procedures for visibility on ICT risks and incidents.
- Ensure adequate resources, funding, and cross-departmental collaboration.
With alignment comes accountability and efficient, holistic governance—the cornerstone for sustained resilience.
DORA Compliance Tip 7: Track the Timeline and Ensure Full Readiness
Remember—the clock is ticking. DORA entered into force on January 16, 2023, with all financial entities expected to comply fully by January 17, 2025 (Eur-lex).
Stay compliant with our DORA compliance services by:
- Regularly monitoring internal milestones.
- Being open to strategy adjustments early.
- Maintaining ongoing communication with regulatory authorities.
Sticking rigorously to DORA timelines isn’t just good compliance—it’s also prudent, proactive risk management.
Final Tip & Wrap-Up
At its heart, DORA is more than regulatory red tape—it’s your opportunity to concretely strengthen digital resilience, enhance customer trust, and sharpen strategic competitiveness.
Stay consistently informed, flexible, and adaptive. Because ultimately, compliance with DORA translates not just into legal safety, but into future-proof business advantage in Europe’s evolving digital financial landscape.
Now go out there and make it happen.
