As cybersecurity threats surge globally, the European Union is fortifying its digital defences by introducing robust legislative frameworks. Notable among these are the Cyber Resilience Act (CRA) and the Digital Operational Resilience Act (DORA). Both regulations aim to enhance security and resilience, but—make no mistake—they differ significantly in scope, targets, compliance requirements, reporting mandates, enforcement mechanisms, and implementation timelines.
To successfully navigate these pivotal frameworks, companies must clearly grasp each act’s specific contours. Curious to know exactly where they differ? Let’s dive in.
1. Scope of Application: Cyber Resilience Act and DORA Compared
Let’s start at the source: differences in scope and applicability.
The Digital Operational Resilience Act (DORA) specifically targets Europe’s financial and insurance sectors, mandating that financial institutions, including banks, investment firms, insurance companies, and payment providers, as well as related third-party ICT vendors, establish uniform ICT risk management frameworks. By setting standardised resilience testing and governance procedures, DORA works steadily toward harmonising cyberspace security across Europe’s financial ecosystem (Chambers).
Meanwhile, the scope of the Cyber Resilience Act (CRA) is significantly broader. It applies comprehensively to nearly every digital product placed on the EU market, regardless of industry. From IoT devices and smart appliances to enterprise software and connected industrial equipment, CRA mandates manufacturers, importers, and distributors alike to meet rigorous cybersecurity conformity assessment criteria before bringing products to market (JD Supra). Simply put, while DORA targets finance specifically, CRA casts a far wider net across all digitally connected sectors.
For instance:
- DORA: Banks, insurance providers, payment operators, and ICT vendors specialised for financial services.
- CRA: Makers of smart home products, auto manufacturers embedding digital systems, medical device firms incorporating networked software, and SaaS providers.
By clearly differentiating their targeted sectors, these two acts cooperate to form complementary layers of cybersecurity strength across Europe’s digital economy.
2. Regulatory Objectives: Cyber Resilience Act and DORA Compared
But what’s driving this differentiation beneath the surface? Simple: CRA and DORA have distinctly separate regulatory missions.
DORA aims squarely at operational resilience within financial services. Its goal is to ensure the continuity and stability of critical ICT services crucial for economic well-being. Essentially, it wants to minimise disruption from cyber incidents, creating standardised IT practices and response frameworks to manage and recover quickly (and securely) (Heuking).
In contrast, CRA champions the principle of security-by-design. The act focuses broadly on embedding proactive cybersecurity measures throughout the digital product lifecycle. It requires digital goods to undergo strictly enforced conformity assessments and operate with ongoing vulnerability management practices—essentially catching cybersecurity flaws at the earliest stages possible, well before market release (Everbridge).
In short, DORA safeguards financial continuity and resilience; CRA promotes systemic, preventative security across all connected products.
3. Target Entities: Cyber Resilience Act and DORA Compared
Consequently, each act regulates different types of entities.
- DORA specifically focuses on financial institutions (banks, insurers, investment firms, payment providers) and the third-party ICT firms serving these organisations.
- CRA widely applies to digital product manufacturers, importers, distributors, software developers, and SaaS/firmware providers operating across all EU markets.
So, an ICT vendor specialising in software used solely by banks falls under DORA; a manufacturer producing IoT consumer electronics or medical technology is squarely under CRA’s watch (JD Supra).
4. Compliance Requirements: Cyber Resilience Act and DORA Compared
Given their distinct scopes, compliance obligations under each act differ precisely:
- Under DORA, financial entities must develop thorough ICT governance policies, conduct ongoing resilience and penetration testing, and set rigorous controls for third-party ICT partnerships (Heuking).
👉 Need hands-on help? Check out our in-house DORA compliance services for a proven, step-by-step implementation playbook.
- In contrast, the CRA mandates formal cybersecurity conformity assessments for digital products, frequent vulnerability evaluations, and security-by-design documentation standards from manufacturers and distributors across all sectors.
The result? DORA commands continual resilience and third-party management in finance; CRA calls for end-to-end proactive product cybersecurity.
5. Incident Reporting Mandates: Cyber Resilience Act and DORA Compared
Incident reporting timelines present yet another key differentiator between the acts.
Under DORA, reporting cyber incidents quickly to national financial regulators is critical—but initial timelines are relatively flexible, with instances like ICT service outages requiring prompt notification and responsive action (Chambers).
Meanwhile, CRA significantly tightens timelines, specifying incidents involving exploited vulnerabilities must be reported to authorities (ENISA and national CERTs) within a strict 24-hour window, followed by detailed progress reports throughout the incident lifecycle (JD Supra).
Thus, compared with DORA’s relatively more adaptive yet still rigorous regime, CRA imposes stricter, highly prescriptive reporting mandates.
6. Enforcement and Penalties: Cyber Resilience Act and DORA Compared
Penalties differ noticeably, too.
Under DORA, financial service regulators apply context-specific supervisory actions and fines with amounts depending primarily on institution size, impact severity, and repeat non-compliance.
On the flip side, the CRA comes with explicitly defined penalties linked directly to global annual turnover, ranging from €5 million (or 1%) up to €15 million (or 2.5%) for the most severe breaches. This structure explicitly aims for deterrence among manufacturers and distributors of digital products everywhere.
What’s more, CRA involves broader EU-level collaboration among ENISA and national authorities, leading to enhanced cross-border enforcement actions, including potential product recalls and prohibition.
7. Timelines and Implementation: Cyber Resilience Act and DORA Compared
In terms of timelines, DORA already entered into force on January 17, 2023, giving financial entities exactly two years (until January 17, 2025) to align their operational resilience measures (Heuking).
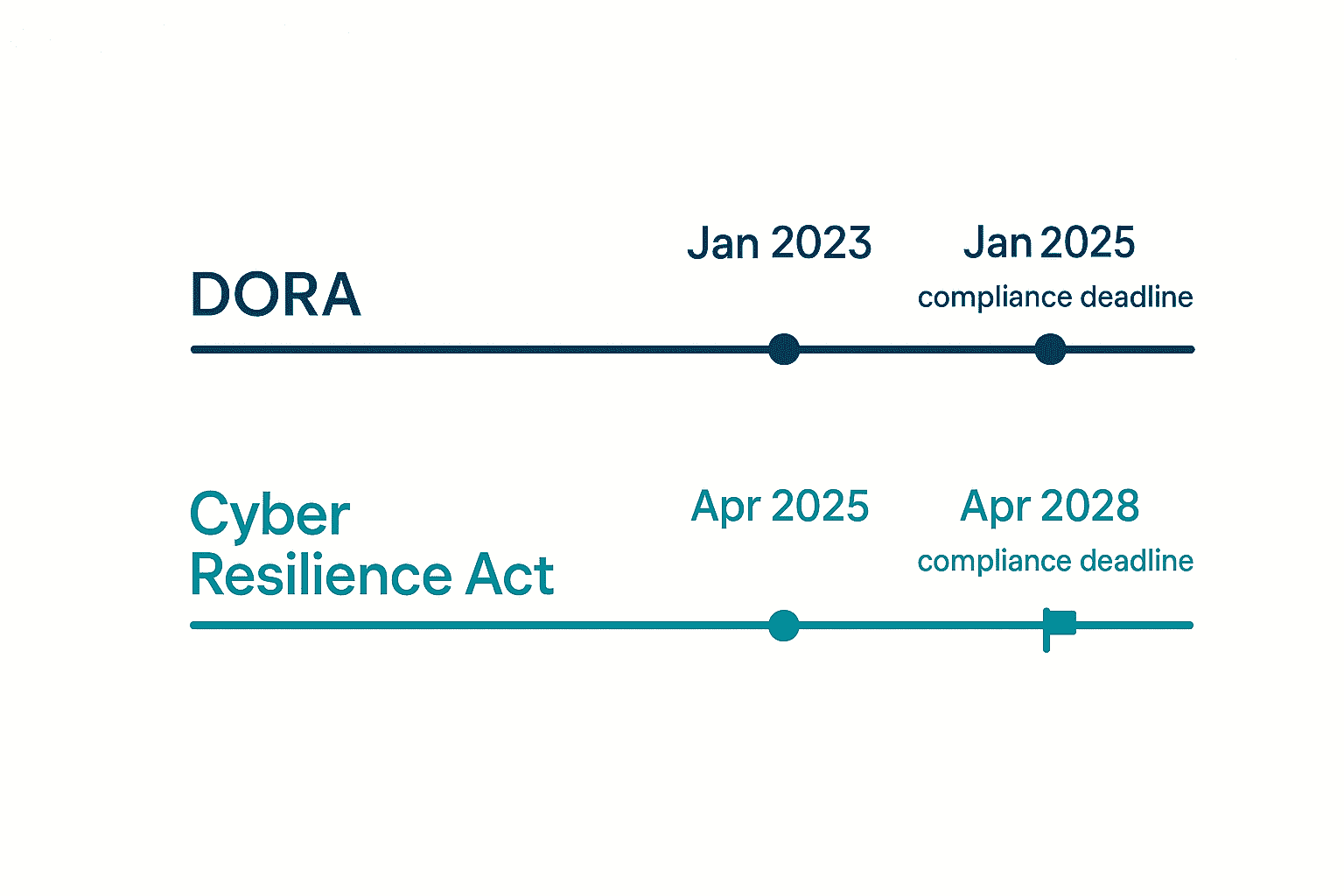
Meanwhile, the CRA is currently progressing through EU legislative channels, and after its recent approval by the European Parliament in March 2024, full adoption (expected soon) should give businesses roughly 36 months from official publication to formal implementation (JD Supra).
Seemingly far away—but remember, preparation begins today.
Final Insights and Wrap-up
While both DORA and CRA pursue stronger EU cybersecurity, the two acts differ significantly in their emphasis: operational resilience in the finance sector (DORA), and security-by-design regulation for digital products across sectors (CRA).
Organisations must anticipate potential overlaps that industry groups (such as AFME) have already highlighted. Accordingly, a proactive compliance strategy—combined with early discussions with regulatory bodies—is recommended.
So here’s the bottom line:
- If you’re in financial services, prioritise DORA readiness.
- If you’re manufacturing or supplying digital products, prepare for the CRA’s lifecycle cybersecurity requirements.
Either way, proactively engaging with these legislations now will position your organisation strongly in Europe’s increasingly regulated digital future.
Ready to get started? The clock is ticking—so let’s get to work!
