DORA requirements (Regulation (EU) 2022/2554) have been legally binding since 17 January 2025, forcing every EU bank, insurer, payment firm and critical ICT supplier to prove real-time cyber resilience. Falling short now risks fines, licence restrictions and reputational damage.
Below are 10 proven tips you can’t ignore in 2025. They will help you align policy documents, tighten incident reporting, stress-test third-party vendors and turn DORA compliance into a competitive advantage rather than a firefight.

1. Understand the Scope and Objectives of DORA
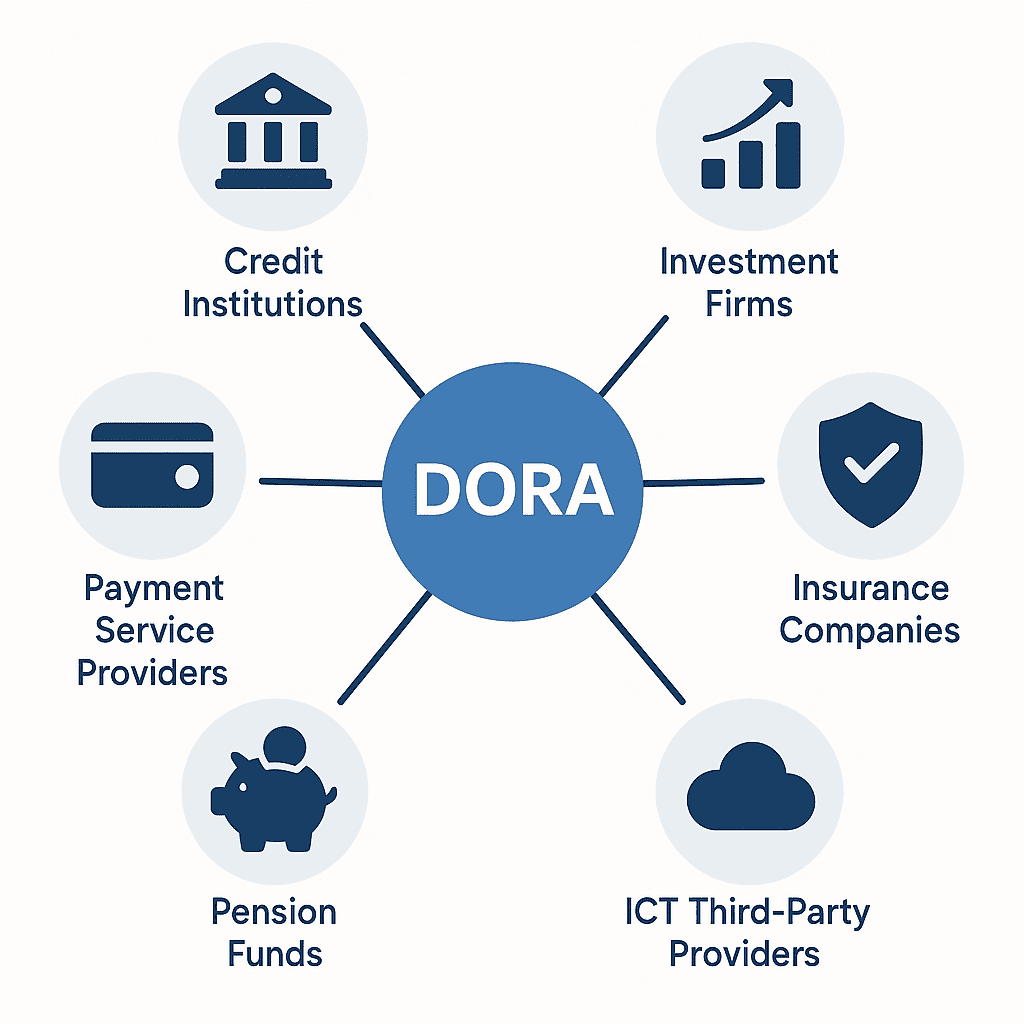
The Digital Operational Resilience Act (Regulation (EU) 2022/2554) establishes uniform cybersecurity standards for financial entities operating within the EU. This act sets forth clearly defined expectations around managing digital risks and disruptions — whether from cyber incidents, technology outages, or system vulnerabilities Wikipedia.
Specifically, organisations critical to Europe’s financial stability fall under DORA’s jurisdiction, including:
- Banks, credit institutions, and investment firms
- Insurance providers and intermediaries
- Trading venues
- Payment and e-money institutions
- Crypto-asset service providers
Collectively, these obligations are known as the DORA requirements, and satisfying them is essential for digital resilience.
As if that’s not enough, third-party ICT service providers critical to financial entities also become directly accountable under the DORA requirements. If your company provides software platforms, cloud services, or technical functions integral to the financial sector, DORA has you covered.
A cornerstone of this regulation is the principle of proportionality. Smaller institutions with lower risk profiles benefit from scaled-down compliance measures relative to large, complex entities. Imagine a small fintech leveraging standard cloud services—it will face streamlined regulatory demands compared to international banks operating proprietary systems vulnerable to sophisticated threats.
Clearly grasping the nuances in scope and objectives allows your organisation to strategically streamline resource allocation, risk management policies, and cybersecurity controls. With a firm foundation laid, DORA compliance moves from a regulatory chore into a genuine opportunity to build resilience.
2. Tailor Your ICT Risk Management Framework
Now let’s get down to business. To fully align with DORA, your ICT risk management framework must reflect your organisation’s size, complexity, and operational specifics.
Conduct Thorough Assessments to Evaluate ICT Risks
Your ICT risk management begins with comprehensive assessments. Clearly map key assets, applications, systems, and data. Document potential threats—external and internal—and regularly reassess as technologies, contexts, and threats evolve. Consider applying standardised methodologies like ISO/IEC 27005 or NIST SP 800-30 for rigorous risk quantification.
Picture this: a financial institution running ransomware simulations to test scenarios related to data breaches, financial impacts, regulatory fines, and downtime consequences. Such exercises help sharpen your defensive readiness. Regular rehearsals also prove that your controls already match the DORA requirements that auditors will review.
Establish Clear Structures for Monitoring and Governance
Clearly defined roles and responsibilities are essential to ICT governance DORA requirements. Appointing senior executives accountable for digital resilience, such as a Chief Information Security Officer (CISO) or Chief Risk Officer (CRO)—makes your compliance efforts transparent and structured.
Leveraging technology-based monitoring tools like Security Information and Event Management (SIEM) and Security Orchestration Automation and Response (SOAR) systems enhances your proactive detection capabilities. Regular supervisory committees, like a monthly ICT Risk Committee, maintain oversight.
Systematically Document Risk Mitigation Efforts
Careful, ongoing documentation of mitigations is required by DORA requirements. A clear, documented ICT risk register provides transparency. Record your decision-making processes—risk appetites, priorities, and resource allocation. This centralised documentation clarifies remediation efforts and aids regulatory reporting.
3. Key DORA Requirements for Incident Reporting
Let’s dive deeper. Prompt incident reporting matters drastically. DORA mandates swift reporting of significant ICT incidents to supervisory authorities.
Adopt Standardised Templates
Clearly structured templates speed up your reporting processes. Include critical details—incident type, date and time detected, systems affected, financial and operational impact, recovery timelines, and contact information. Regulators like ESMA and national authorities (e.g., BaFin or FCA) provide useful template guidance.
Define Clear Thresholds
Set explicit criteria defining what constitutes a “major” incident, triggering external notifications. This swift escalation capability ensures no critical incidents slip through the cracks. Criteria may involve disruption scope, outage duration, financial impact, systemic implications, and broader financial reputational effects.
Integrate with Business Continuity Planning (BCP)
Efficient incident procedures must closely integrate into your business continuity plans. Regular tabletop exercises and simulations build familiarity and preparedness, turning crisis response into second nature within your organisation. Documenting and rehearsing these workflows cements compliance with the DORA requirements for timely incident reporting.
4. Implement Robust Digital Operational Resilience Testing
Systematic resilience testing moves compliance far beyond mere checklists. DORA requirements, continuous testing identifies vulnerabilities before cyber incidents happen.
Create Regular Testing Programs
Your testing framework should include penetration tests and realistic simulations (like Red Team vs. Blue Team exercises). Such tests vividly demonstrate weaknesses and defensive gaps, preparing your team against real threats.
Carefully Document Testing Outcomes
Comprehensive records foster transparency, systematically documenting test scope, methodology, vulnerabilities uncovered, and corrective actions taken.
Leverage Continuous Improvement
Testing creates a feedback loop: The lessons learned keep shaping your cybersecurity policies, incident response procedures, and operational workflows—ultimately driving sustained improvements to your resilience infrastructure.
5. Managing Vendors Under DORA Requirements
The challenge? Third-party vendors sometimes inadvertently introduce cybersecurity risks. Managing these relationships proactively is crucial DORA requirements.
Rigorous Vendor Vetting and Audits
Focus especially on critical ICT vendors: conduct extensive pre-onboarding due diligence, continuous audits, and ensure “right-to-audit” contract clauses. Utilise frameworks like SOC 2 and ISO 27001 standards for vetting and auditing.
Strategic Contractual Alignment with DORA
Clearly outline obligations, SLAs, incident notification requirements, and exit strategies in ICT contracts. Explicit notification timelines (e.g., 12-24 hours from serious breaches) augment accountability and encourage proactive compliance.
Continuous Vendor Risk Updates
Regularly stay abreast of changes in vendor structures, industry incidents, or vulnerabilities, adjusting vendor risk assessments as needed. Actively collaborate and communicate with third-party providers to enhance mutual resilience efforts. This continuous oversight shows stakeholders that even outsourced services respect the DORA requirements.
6. Establish Clear Vulnerability Coordination and Disclosure Mechanisms
DORA mandates precise vulnerability coordination. Structured disclosure processes streamline your efforts to quickly notify supervisory authorities about exploited risks.
Use clear disclosure timelines aligned with vulnerability severity and exploitation activity, standardised reporting templates, vulnerability coordinators, and designated communication channels (e.g., a secure reporting email). These frameworks significantly speed vulnerability response times and reduce ambiguity.
7. Promote Information Sharing and Collaboration
Want to level up your resilience even further? Regularly collaborate with industry consortia, cybersecurity forums, or Computer Emergency Response Teams (CERTs). Actively engaging with platforms like FS-ISAC, CSIRTs, and the Malware Information Sharing Platform (MISP) amplifies threat detection capacities across the EU financial sector, keeping you steps ahead of emerging threats.
8. Leverage Standardised Security Data Architectures
Complex ecosystems demand clear data architectures. Embrace architectures such as SecDOAR or adopt formats such as STIX/TAXII to standardise your security data frameworks. Doing this simplifies your security information and incident management practices, enhancing the speed and accuracy of threat detection. In practice, standardisation makes fulfilling the DORA requirements far easier to evidence.
9. DevOps Metrics That Prove DORA Requirements Success
Benchmarking your operational resilience using DevOps metrics—deployment frequency, lead time for changes, MTTR, and change failure rate—demonstrably improves your readiness in the face of operational disruptions.
Regularly comparing your metrics to peer organisations ensures your cybersecurity standards remain robust, aligns actions clearly with regulatory compliance, and incentivises continuous improvement through clear feedback loops within your DevOps frameworks.
10. Stay Informed about Emerging Technical Standards
DORA is evolving. European Supervisory Authorities (ESAs) release new Regulatory Technical Standards (RTS) and Implementing Technical Standards (ITS) periodically. Establish cross-functional teams to continually monitor ESA communication, proactively adjusting your internal policies to emerging technical standards. Attending peer workshops, industry forums, and ESA updates ensures you are always outperforming DORA regulatory requirements.
By aligning strategy, tooling and culture with the DORA requirements, you future-proof operations against regulatory shocks.
Wrap-Up: Embed a Culture of Cyber-Resilience
Here’s the kicker: Embedding cybersecurity by design within your organisational culture profoundly transforms DORA compliance into strategic resilience. Proactively aligning with DORA not only ensures regulatory success, but also fundamentally strengthens your organisation’s entire cybersecurity stance—ultimately reducing overall digital operational risks Arxiv.
So go ahead—embrace these steps, align your processes, and become truly resilient. Can you afford not to?
