As the CTO of a growing Small or Medium-sized Business (SMB) in the tech sector, understanding the IT Security Audit process is crucial. You’re juggling innovation, development cycles, infrastructure management, and team leadership. It’s easy for cybersecurity to feel like just another item on an endless list. However, in today’s threat landscape, a proactive approach to security isn’t optional—it’s fundamental. A cornerstone of this proactive stance? The comprehensive IT Security Audit.
Ignoring this critical process is like building a cutting-edge tech product on shaky foundations. For SMB tech companies, the stakes are particularly high. You handle sensitive client data, proprietary code, and intellectual property – all prime targets for cybercriminals. A single breach can lead to devastating financial losses, reputational damage, loss of client trust, and potentially crippling legal liabilities.
This guide provides practical insights into IT security audits, specifically for leaders like you.
What Exactly is an IT Security Audit?
An IT Security Audit is a systematic, measurable technical assessment of your company’s IT infrastructure, applications, data-handling processes, and security practices. It’s not just a quick scan; it’s a deep dive designed to:
- Identify Vulnerabilities: Pinpoint weaknesses in your systems, networks, software, and configurations before attackers can exploit them.
- Assess Risks: Identify vulnerabilities’ potential impact and prioritize remediation efforts.
- Verify Compliance: Ensure your security practices meet relevant industry standards (like SOC 2, ISO 27001, GDPR, and CCPA) and contractual obligations.
- Evaluate Controls: Determine if your existing security measures (firewalls, access controls, encryption, etc.) are effective and properly implemented.
- Benchmark Performance: Compare your security posture against best practices and identify areas for improvement.
Why an IT Security Audit is Crucial for Your SMB Tech Company
- Protecting IP and Client Data: Your core assets are digital. An audit helps safeguard your code, algorithms, and the sensitive data entrusted to you by clients.
- Meeting Client Expectations: Increasingly, clients (especially larger enterprises) demand proof of robust security practices before engaging with tech vendors. An audit report can be a key differentiator.
- Ensuring Business Continuity: Downtime caused by a security incident can halt development, disrupt services, and cost dearly. Audits help prevent these disruptions.
- Compliance Requirements: Depending on your niche and clientele, you may be legally or contractually obligated to perform regular security audits.
- Resource Optimization: While audits cost time and money, they are far less expensive than recovering from a major breach. They help you focus security spending where it’s most needed.
- Building Investor Confidence: Demonstrating a mature security posture can be vital when seeking funding or partnerships.
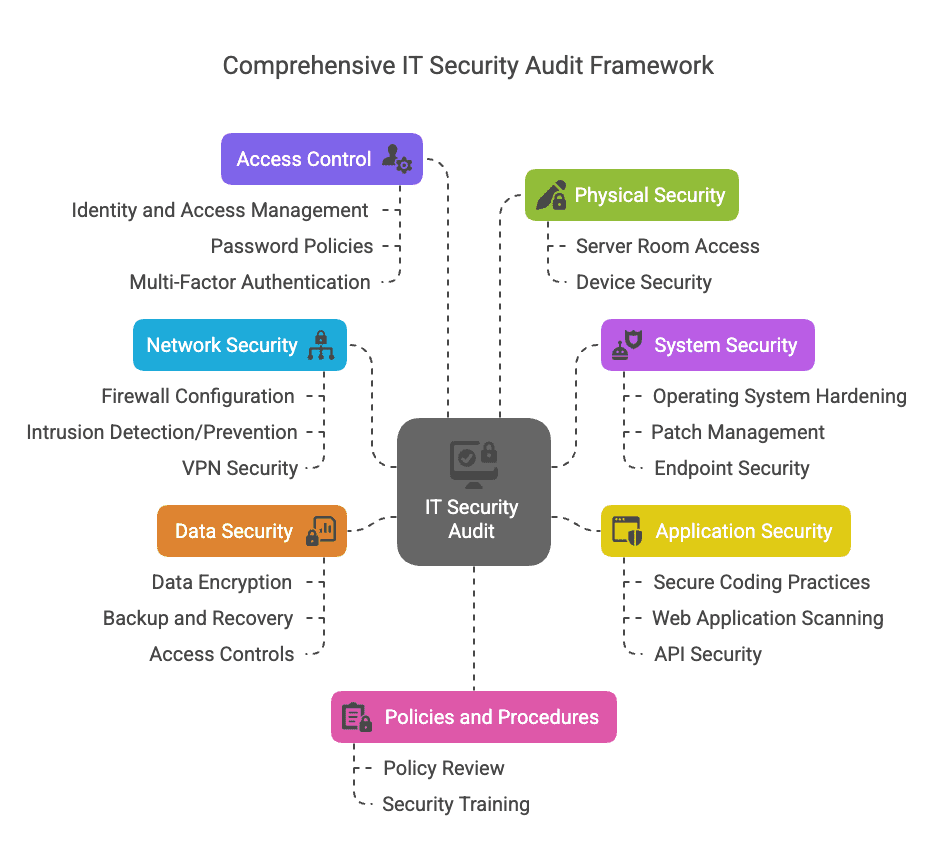
Key Components of a Comprehensive IT Security Audit
A thorough IT Security Audit typically examines multiple layers:
- Network Security:
- Firewall configuration and rule sets.
- Intrusion Detection/Prevention Systems (IDS/IPS).
- VPN and remote access security.
- Wireless network security (Wi-Fi).
- Network segmentation.
- System Security:
- Operating system hardening (servers, workstations).
- Patch management processes.
- Endpoint security (antivirus, EDR).
- Server configurations (web, database, application servers).
- Application Security:
- Secure coding practices (review processes).
- Web application vulnerability scanning (SQL injection, XSS, etc.).
- API security.
- Third-party software security.
- Data Security:
- Data encryption (at rest and in transit).
- Data backup and recovery procedures.
- Data access controls and permissions.
- Data loss prevention (DLP) measures.
- Access Control:
- Identity and Access Management (IAM) systems.
- Password policies and multi-factor authentication (MFA).
- Privileged Access Management (PAM).
- User account review and de-provisioning processes.
- Physical Security: (Often overlooked but crucial)
- Access to server rooms and data centers.
- Device security (laptops, mobile devices).
- Policies and Procedures:
- Review of security policies (Acceptable Use, Incident Response Plan, Disaster Recovery Plan).
- Security awareness training effectiveness.
Types of IT Security Audits
Understanding the different types helps tailor the approach:
- Vulnerability Assessment: Uses automated tools to scan for known vulnerabilities. Good for regular check-ups.
- Penetration Testing (Pen Test): Simulates real-world attacks to actively exploit vulnerabilities. More in-depth and reveals exploitability.
- Compliance Audit: Focuses specifically on meeting the requirements of standards like ISO 27001, SOC 2, HIPAA, GDPR, etc. (Consider linking externally here, e.g., to iso.org or similar authoritative sources for compliance standards).
- Internal Audit: Conducted by your team. Useful for continuous improvement but may lack objectivity.
- External Audit: Performed by a third-party security firm. Provides an unbiased, expert perspective and is often required for compliance or client assurance.
The IT Security Audit Process: A 6-Step Practical Roadmap
Executing an effective IT Security Audit involves these key stages:
- Planning & Scoping:
- Define clear objectives (e.g., assess web app security, prepare for SOC 2).
- Determine the scope (which systems, networks, and applications are included?).
- Identify key stakeholders.
- Choose the audit type(s) and methodology.
- Select an auditor (internal team or external firm).
- Information Gathering & Documentation Review:
- Auditors collect network diagrams, policies, previous reports, and system configurations.
- Interviews with key IT and development staff.
- Technical Testing & Evaluation:
- Running scans (vulnerability assessment).
- Attempting exploits (penetration testing).
- Reviewing configurations and logs.
- Verifying access controls and permissions.
- Analysis & Reporting:
- Auditors analyze findings, correlating data from different tests.
- Prioritize vulnerabilities based on severity and exploitability.
- Develop a detailed report including:
- Executive Summary (for non-technical stakeholders).
- Detailed Findings (vulnerabilities, evidence).
- Risk Assessment.
- Actionable Remediation Recommendations.
- Remediation:
- Your team develops a plan to address the findings.
- Implement fixes, patches, configuration changes, and policy updates.
- Prioritize based on the audit report’s risk assessment.
- Verification & Follow-up:
- Auditors (or your internal team) verify that the remediation actions were successful.
- Schedule follow-up audits to ensure ongoing security posture.
Internal vs. External Audits: Making the Right Choice for Your IT Security Audit
- Internal Audits: Cost-effective for routine checks, leverage internal knowledge. However, they can suffer from bias, lack of specialized expertise, and limited resources.
- External Audits: They offer independence, specialized skills, broader industry perspective, and credibility (essential for compliance/client trust). They are generally more expensive. Engaging a specialized firm ensures you benefit from dedicated expertise and up-to-date knowledge of the threat landscape; explore professional IT security audit options to see how they fit your needs.
Recommendation for CTOs: A hybrid approach often works best. Use internal resources for regular vulnerability scanning and policy checks. Engage external experts for periodic, in-depth penetration tests and critical compliance audits (e.g., annually or biennially).
Common IT Security Audit Pitfalls to Avoid
- Poor Scoping: Auditing too little (missing critical systems) or too much (wasting resources).
- Treating it as a Checkbox: Focusing only on compliance, not actual security improvement.
- Ignoring the Report: Failing to act on the findings and recommendations. Remediation is key!
- Lack of Communication: Poor coordination between the audit team and your internal staff.
- Infrequent Audits: The threat landscape changes rapidly; audits should be performed regularly.
Beyond Security: The Added Benefits of an IT Security Audit
A well-executed IT Security Audit delivers more than just vulnerability patching:
- Increased Client Trust: Demonstrates commitment to protecting data.
- Improved Operational Efficiency: Often identifies configuration issues that impact performance.
- Enhanced Compliance Posture: Reduces the risk of fines and penalties.
- Informed Budgeting: Justifies security investments and directs spending effectively.
Take Action: Secure Your Future
As a CTO in the fast-paced tech world, you understand the importance of robust systems. An IT Security Audit isn’t an expense; it’s an investment in your company’s resilience, reputation, and future success. Don’t wait for a breach to highlight your weaknesses.
Ready to strengthen your defenses? Learn more about how our expert IT Security Audit services can help protect your SMB tech company. Schedule a consultation today to discuss your specific needs.