PCI-DSS Importance is skyrocketing in 2025, and version 4.0.1 is the fastest route to safer card data—here’s why.
PCI-DSS 4.0.1 may look like a simple “dot” release, yet its tighter wording can shave weeks off an audit and close cracks that attackers still exploit. Ready to see how? Let’s dive in.
PCI-DSS version 4.0.1 keeps all 64 controls introduced in 4.0. It simply rewrites confusing sentences, updates testing steps, and clarifies rules for firewalls, keyed hashing, 30-day critical patching, and phishing-resistant MFA. Because assessors can certify against 4.0.1 today—and because version 4.0 retires on 31 Dec 2025—every business that stores, processes, or transmits card data should switch now. Early movers report three big wins: lighter evidence packs, smaller breach-response fines, and louder customer trust.
PCI-DSS at a Glance
What the Standard Protects
Cardholder data crosses five predictable stops—swipe, transit, authorisation, settlement, storage. PCI-DSS shields each one.
• Merchants & retailers: POS terminals, mobile readers, e-commerce carts.
• Payment processors & gateways: switch networks, tokenisation engines.
• Service providers: cloud hosts, call centres, managed firewalls.
By enforcing the same safeguards everywhere, PCI-DSS 4.0.1 slashes breach odds and keeps incident costs low—key reasons PCI-DSS 4.0.1 matters to every card-handling entity.
How We Reached 4.0.1
| Year | Version | Why It Mattered |
| 2004 | 1.0 | First unified card-scheme standard. |
| 2010 | 2.0 | Added risk-based language for flexibility. |
| 2016 | 3.2.1 | Forced TLS 1.2, improved service-provider logging. |
| 2022 | 4.0 | Added 64 modern requirements and custom-control options. |
| 2024 | 4.0.1 | Fixed typos, refined MFA, clarified hashing—no new controls. |
The key change in PCI-DSS 4.0.1 vs 4.0 is clarity. Clear text means fewer assessor debates, faster sign-off, and lower QSA fees—a direct impact on businesses.
Jargon You’ll Meet
• Clarification: wording tweak, zero extra effort.
• Applicability Note: tells you when a rule applies.
• Targeted Risk Analysis (TRA): your custom risk study when timing or method is flexible.
• Phishing-resistant factor: an authenticator (e.g., FIDO2 passkey) immune to replay and proxy attacks.
Master these terms first; they anchor any PCI-DSS 4.0.1 compliance guide.
What’s New in PCI-DSS v4.0.1
High-Level Differences
Nine updates headline the release:
- Keyed hashing scope clarified.
- 30-day patch window limited to critical (CVSS ≥ 9) flaws.
- A phishing-resistant factor alone now satisfies MFA.
- Firewall language widened for cloud and micro-segmentation.
- Typos, broken links, and errata fixed.
- New applicability notes kill past confusion.
- Testing steps mapped to real-world evidence.
- Glossary tightened; terms like “passphrase” cleaned up.
- Appendix D lists sample artefacts per control.
Bottom line? Less ambiguity, smoother audits—proving the benefits of PCI-DSS 4.0.1 compliance are very real.
Change Log Highlights
| Requirement | Change | Why It Matters | Real-World Win |
| 1 – Network Security | “Firewalls must be stateful” → “Network security controls must inspect and control traffic.” | Let you use cloud security groups or micro-seg tools. | A retailer running Kubernetes on AWS shows security-group rules instead of legacy firewalls. |
| 3 – Cryptographic Hashes | Keyed hashing is required only when hashes gate access, not when they just verify integrity. | Stops over-scoping of log-integrity tools. | Merchants keep SHA-256 integrity hashes unkeyed, saving dev time. |
| 6 – Patching | 30-day SLA now for critical vulns only; others need a TRA. | Focuses ops on real risks. | A gateway can justify 60 days for a medium bug with no PAN exposure. |
| 8 – Authentication | A single phishing-resistant factor = MFA. | Cuts login friction. | Processors issue YubiKeys; SMS codes disappear. |
| Appendices | Test scripts renamed “Testing Procedures,” sample evidence added. | Sets clear assessor expectations. | QSAs accept Terraform plans in place of screenshots. |
Parallel-Run Timeline
- Both 4.0 and 4.0.1 are valid until 31 Dec 2025.
- Pick one version per audit; QSAs accept either.
- From 1 Jan 2026, only 4.0.1 (or later) counts.
If your audit is already halfway done, finish on 4.0. Otherwise, jump to 4.0.1 and bank the clarifications.
Why PCI-DSS v4.0.1 Matters
Security Improvements
Even with no new controls, sharper text drives real risk reduction.
- Keyed-hash strength now must match encryption strength—bye-bye SHA-1.
- Clear MFA rules let you drop weak OTPs once you adopt FIDO2.
- Updated testing steps push “evidence any time,” nudging teams toward automated scans.
That trio alone delivers measurable PCI-DSS 4.0.1 risk reduction.
Business Value
- Smaller breach scope, lower fines.
- Higher customer trust—up-to-date attestations reassure shoppers.
- Faster partner onboarding—acquirers love clear wording.
- Audit efficiency—continuous evidence slashes overtime.
Those benefits prove the impact of PCI-DSS 4.0.1 on businesses is anything but minor.
Competitive & Regulatory Alignment
PCI-DSS 4.0.1 now echoes NIST CSF, ISO 27001, and EU-DORA timelines. Cross-mapping grows simpler, giving global payment firms a head start.
Benefits of Early Adoption
Smoother Year-End Audits
A midsize retailer piloting 4.0.1 saw 30 % fewer QSA questions and cut four billable days. How can you beat that?
Time to Modernise Legacy Tech
Use the breathing room to:
- Swap SHA-1 for HMAC-SHA-256.
- Automate 30-day critical patch tickets.
- Pilot phishing-resistant keys for admins.
Modernising during a “clarification” cycle is cheaper than during a major overhaul.
Lighter Evidence Requests
Point to new applicability notes to keep non-CDE servers out of sample sets. Offer continuous-compliance dashboards. Result? Less manual work, smaller QSA invoice.
Stakeholder Impact Deep-Dive
PCI-DSS Importance for Merchants & Retailers
PCI-DSS 4.0.1 lets you drop keyed hashes when you store only tokens or truncated PANs. One apparel chain deleted legacy hash columns and shrank its ROC narrative from 12 pages to three. That’s PCI-DSS 4.0.1 for retailers in action.
Payment Processors & Gateways
FIDO2 keys now satisfy MFA alone. A gateway with 900 staff cut help-desk resets by 38 % and trimmed ROC sampling from three days to one. Talk about PCI-DSS 4.0.1 adoption benefits.
SaaS & Third-Party Providers
Sharper applicability notes force every shared-responsibility matrix to update. Vendors that post the new matrix in customer portals watch contract redlines vanish.
Four-Phase Implementation Roadmap
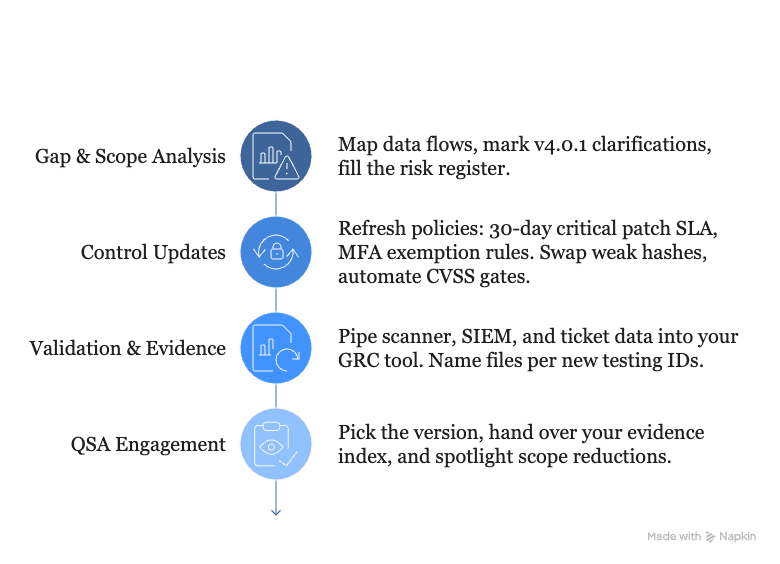
- Gap & Scope Analysis – Map data flows, mark v4.0.1 clarifications, fill the risk register.
- Control Updates – Refresh policies: 30-day critical patch SLA, MFA exemption rules. Swap weak hashes, automate CVSS gates.
- Validation & Evidence – Pipe scanner, SIEM, and ticket data into your GRC tool. Name files per new testing IDs.
- QSA Engagement – Pick the version, hand over your evidence index, and spotlight scope reductions.
Follow this PCI-DSS 4.0.1 compliance checklist and you’re golden.
Technical Best Practices
Keyed Hashing
Move to HMAC-SHA-256, rotate keys every 12–18 months, and document the cryptoperiod. Yes, it’s that simple.
CVSS-Driven Patching
Auto-tag CVSS ≥ 9 findings, set a 30-day deadline, and watch MTTR charts improve.
Phishing-Resistant Authentication
Issue FIDO2 tokens, enable WebAuthn, block weak factors, and record exceptions. Result? PCI-DSS 4.0.1 security improvements without user complaints.
Continuous Compliance
Build controls into the pipeline—IaC scans, nightly SLA checks, immutable evidence buckets. Now audits become push-button events.
Common Pitfalls & How to Avoid Them
- Treating the 30-Day Rule as a Free Pass – Medium risks still need a plan. Automate severity-based SLAs.
- Calling Every FIDO Key “Phishing-Resistant” – Only FIDO2/WebAuthn with origin binding qualifies. Validate attestation.
- Skipping Third-Party Matrices – Update contracts or risk failing Requirement 12.
Dodge these traps, and the benefits of PCI-DSS 4.0.1 compliance stay intact.
Future Outlook
- Expect annual dot-releases through 2028—light edits, no new controls.
- PCI-DSS v5.0 may land around 2028 with passwordless defaults and a deeper cloud focus.
- AI-powered threat modelling could soon satisfy Requirement 12 risk assessments.
Stay agile: track dot-releases, pilot AI in a sandbox, and phrase policies to reference “current PCI-DSS requirements.”
Additional Resources
- PCI DSS v4.0.1 Standard (PDF)
- “Just Published: PCI DSS v4.0.1” – PCI SSC blog
- “PCI DSS v4.0.1: Key Updates You Need to Know” – RSI Security
- vCISO services – hands-on PCI-DSS 4.0.1 support – CyAdviso
Conclusion
In short, PCI-DSS 4.0.1 is a housekeeping update that packs heavyweight value. Adopt it now and you gain:
- Lean policies that mirror the clarified text.
- Faster audits and partner onboarding.
- Concrete PCI-DSS 4.0.1 risk reduction through stronger hashing, smarter patching, and simpler MFA.
So what are you waiting for? Migrate to PCI-DSS 4.0.1, lock in the wins, and show customers their card data couldn’t be safer.
