This SWIFT CSP checklist distils everything you need for a flawless 2025 audit. By following the checklist below, you can tick every mandatory control with confidence and speed.
As cyber threats continue to evolve dramatically, SWIFT’s Customer Security Programme (CSP) keeps pace, regularly updating its security framework to ensure the resilience and integrity of global financial networks. By 2025, significant adjustments—including stricter third-party management requirements and new mandatory controls—mean financial institutions must begin early preparation. So, how can you effectively align your organisation’s compliance efforts? Let’s dive into these solid, actionable tips that will guide you through the CSP compliance maze.
1. Building Your SWIFT CSP Checklist: Where to Begin
The updated SWIFT Customer Security Controls Framework (CSCF) for 2025 brings substantial enhancements designed to strengthen cybersecurity across the financial services industry. Out of 32 controls, 26 are now mandatory—the highest proportion yet. Clearly, SWIFT isn’t messing around when it comes to security standards.
Two newly introduced controls especially stand out:
-
Control 2.8 – Outsourced Critical Activity Protection: Acknowledging escalating third-party risks, SWIFT now mandates firm protocols to oversee external service providers. This means implementing stringent third-party risk management strategies aligned directly with SWIFT’s own principles.
-
Control 2.4A – Securing Data Flows from Backend Systems: SWIFT emphasises protecting data flows between backend systems and your SWIFT environment, now requiring encryption and stringent segmentation to mitigate vulnerabilities from internal or legacy applications.
To seamlessly adopt these updated controls, follow these structured steps:
-
Conduct a Comprehensive Review: Evaluate each CSCF control against your existing infrastructure to quickly pinpoint gaps requiring immediate attention.
-
Engage Internal Stakeholders: Regular briefings with IT, security, compliance, legal, and operational teams ensure everyone is well-informed and aligned.
-
Update Policies and Procedures: Clearly document enhanced responsibilities regarding new controls, ensuring transparency and accountability within your governance framework.
-
Establish Actionable Compliance Plans: Identify specific tasks, responsible parties, and deadlines to methodically achieve compliance goals, placing priority on the new CSP requirements.
By proactively becoming familiar with the CSCF for 2025, you mitigate compliance risks while building robust defences against evolving threats. For further details, see the SWIFT CSP Framework.
2. Perform Comprehensive Risk Assessments
Now, let’s get down to business. How prepared are you, really? An efficient route toward compliant security begins with meticulously understanding your current baselines and honestly evaluating your gaps.
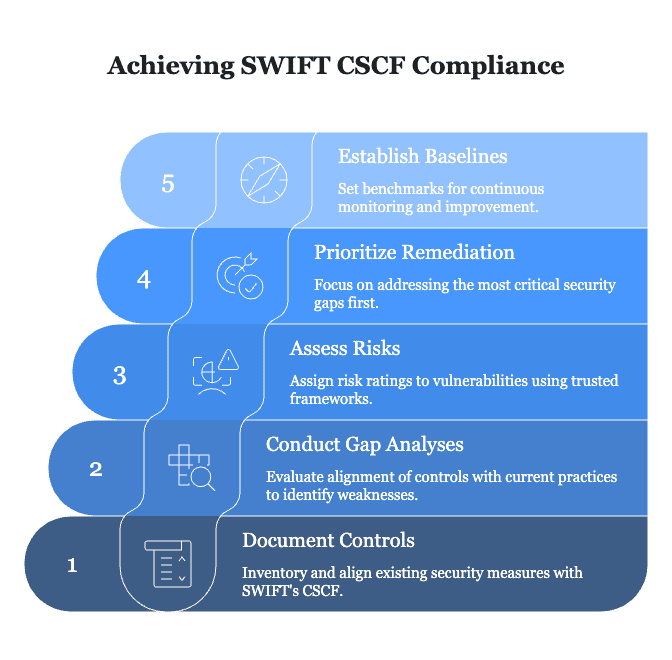
Here’s a practical structure for your comprehensive assessment:
-
Document Existing Controls: First things first—inventory your policies, procedures, and security configurations, aligning everything directly with SWIFT’s CSCF mandatory controls.
-
Detailed Gap Analyses: Don’t pull punches. Evaluate whether each control aligns fully, partially, or not at all with current practices. Clear and honest evaluations here are crucial to meaningful progress.
-
Assess Risks and Impact: Using trusted frameworks like ISO 31000 or NIST 800-30, assign risk ratings and likelihood scores. This way, everyone clearly sees priority vulnerabilities and needed actions.
-
Prioritise Remediation: Always tackle your biggest or most urgent gaps first. Document clear remediation roadmaps—concrete steps, accountable parties, and firm deadlines.
-
Establish Clear Baselines: These objective benchmarks (endpoints, message security, third-party integrations) become your North Star, guiding regular checks and continuous improvements.
Consider an example: A recent assessment finds your teams still depend solely on single-factor remote authentication, clearly non-compliant with Control 4.2. Your action plan? Roll out comprehensive MFA across every SWIFT-related access point immediately.
By staying disciplined and transparent throughout this assessment process, you’ll significantly strengthen your compliance posture and manage cyber risks proactively.
3. Strengthen Third-Party Risk Management
But wait—there’s more. The CSP 2025 significantly expands emphasis on third-party risk management, now elevating Control 2.8 (Outsourced Critical Activity Protection) to mandatory status. It acknowledges that third-party vulnerabilities often directly affect financial institutions.
To successfully address this challenge:
-
Set Comprehensive Policies: Policies must clearly stipulate your security expectations—everything from data handling to incident response.
-
Conduct Regular Vendor Audits: Go beyond policy and periodically verify third-party compliance through structured audits. Remember, trust but verify.
-
Embed TPRM within CSP Attestation: Document third-party security assessments and corrective actions within your annual CSP attestations. It’s the transparency your auditors will look for.
-
Adopt Continuous Risk Monitoring: Implement tools that identify third-party vulnerabilities immediately, providing you with real-time alerts and insights.
-
Formalise Incident Communication: Embed clear guidelines regarding urgent communications and escalations during security incidents originating from third parties.
Adopting these proactive TPRM strategies ensures robust coverage and alignment with SWIFT’s expectations, fortifying your organisation’s outsourced activities against cyber threats.
4. Address Back-Office Security (Control 2.4A)
Back-office vulnerabilities historically serve as tempting targets for attackers. Fortunately, SWIFT’s new Control 2.4A mandates rigorous security specifically for backend data flows and legacy systems.
Essential guidelines include:
-
Encrypt Sensitive Data Flows: Employ robust encryption standards (e.g., TLS 1.3+) across internal communication channels and APIs between backend applications.
-
Segment Your Systems Clearly: Set strict network isolation to contain breaches effectively. Using VLANs, firewalls, and software-defined perimeters significantly diminishes attacker lateral movements.
As an example, isolating payment systems from internal reporting applications through rigorous segmentation provides a simple yet powerful barrier against attackers. Implementing these recommendations now can save tremendous headaches later on.
5. Implement Strict Access Controls
Seriously, how confident are you in your access management? Access control represents a core defensive layer under the new CSP standards. It’s about ensuring appropriate privilege and multi-factor authentication (MFA) across your SWIFT environment.
Take decisive steps:
-
Mandate Multi-Factor Authentication: All user access must include MFA—using tokens, biometrics, or authenticator apps—to satisfy CSP mandates.
-
Review Privileged Access Regularly: Apply the Least Privilege Principle, conduct regular audits, and leverage advanced Privileged Access Management (PAM) systems.
These measures markedly protect you from external threats and insider misuse, both critical for SWIFT compliance.
6. Establish Continuous Monitoring Systems
The watchword in cybersecurity is proactivity. A continuous monitoring system ensures you’re always one step ahead.
To gain this advantage:
-
Deploy advanced threat detection tools (IDS, EDR, SIEM) to spot threats in real-time.
-
Set transparent anomaly reporting with clearly defined escalation processes. Every team member needs clarity on how to respond immediately when an alert triggers.
-
Regularly test incident response plans and integrate these drills fully into actual monitoring solutions, as required by Control 7.1.
Following this structured approach ensures sustained readiness against cyber threats.
7. Align with Global Security Standards and Regulations
But there’s another way to simplify your CSP journey: align with existing security frameworks like ISO 27002, NIST CSF, or regulatory mandates like DORA and NIS2.
Mapping SWIFT controls against globally recognised standards:
- Streamlines compliance efforts
- Provides single-effort documentation usable for multiple audits
- Enhances overall cybersecurity maturity
For example, documenting access controls once through ISO 27002 alignment simultaneously meets SWIFT CSP and regulatory requirements, saving effort and confusion alike.
8. Prepare for Independent Assessments
Never underestimate attestation preparation. SWIFT mandates annual verified compliance reports. Engage auditors early, meticulously document policies and controls, and conduct mock assessments well ahead of deadlines to avoid surprises.
This disciplined approach smooths the independent assessment path, minimising risk and boosting auditor confidence.
9. Utilise Robust Compliance Tools and Resources
Leveraging specialised compliance tools, like IBM’s automated CSP checklist solutions, simplifies tedious audit preparation tasks:
- Automate complex monitoring activities
- Facilitate evidence gathering
- Streamline documentation and report generation
Adopting dedicated compliance tools not only simplifies your processes but ensures consistent readiness for the compliance journey ahead.
Adopting dedicated compliance tools not only simplifies your processes but ensures consistent readiness for the compliance journey ahead.
Need extra hands? Explore our SWIFT CSP services to get turnkey implementation support and stress-free audit prep.
Final Tip – Maintain Constant Vigilance and Readiness
Lastly, staying compliant isn’t a one-time victory—it’s continual discipline. Perform periodic internal audits, provide continual training updates for security teams, and proactively assess infrastructure and third-party vendors regularly.
Ultimately, embedding a proactive security culture safeguards your institution, not just for CSP compliance, but against an ever-evolving landscape of cybersecurity threats.
So what are you waiting for? Start building your 2025 SWIFT CSP readiness today—trust us, you’ll be glad you did.
